Data breaches are the most common cause of email address leaks on the internet, leaving personal data accessible on online forums, the dark web, and other public spaces. According to a 2022 IBM report, it takes an average of 277 days to identify and contain a breach. This means that it may take up to nine months before you become aware that attackers have your personal data.
To minimize the impact of email leaks, it’s essential to regularly check if your personal data has been compromised. In this article, we’ll show you how to check if your email has been leaked and provide actionable steps to protect your online privacy.
What happens if your email is leaked?
In today’s digital age, personal data exposed in data breaches can easily end up on the dark web, leading to a host of problems for victims. If cybercriminals get a hold of your email and password, it can pose a serious threat to the security of your online accounts.
Increased spam and phishing emails
One of the most significant consequences of email leaks is an increase in spam and phishing emails. When your email is leaked, you may notice a sudden surge in unwanted emails flooding your inbox. While spam emails are generally just a nuisance, phishing emails can be far more dangerous. Scammers use these types of emails to impersonate legitimate senders, such as your credit card company or healthcare provider, to trick you into revealing personal information.
Protect your email and personal information by choosing a reliable and secure private mailbox. By doing so, you can minimize the risk of your email being leaked and ensure that your personal information is kept safe from cybercriminals.
One common tactic used by cybercriminals is impersonating the service that has leaked your personal information. Attackers can easily use this information to make their emails appear legitimate, making it difficult for users to detect malicious intent.
This type of attack is called “spear phishing,” and it specifically targets users by impersonating a service, attackers can trick users into revealing sensitive information or downloading malicious attachments.
To protect your email privacy, it’s crucial to remain vigilant against impersonation attacks. Always be wary of emails that request personal information or prompt you to click on links or download attachments, particularly if they claim to be from a service that has experienced a data breach. Consider using a reliable and secure private email service that offers advanced security features, such as two-factor authentication and email aliases, to prevent these types of attacks.
Phishing scams can be a serious threat to your email security, but with a little common sense and vigilance, you can often defend yourself against them.
To stay safe, be on the lookout for any odd-sounding phrases or language in emails you receive. Additionally, carefully inspect the email address of the sender to ensure that it matches the name and address of the company or individual they claim to represent. If you’re unsure about the legitimacy of an email, consider reaching out to the sender via another communication channel to verify their identity.
If you suspect that an email may be a phishing attempt, do not click on any links or download any attachments included in the email. Instead, report the email to your email provider immediately. This can help prevent the spread of phishing attacks and protect your email and personal information from potential threats.
To ensure maximum protection against phishing scams, make use of advanced security features such as advanced machine-learning spam filters, email encryption, and two-factor authentication. This can help minimize the risk of falling victim to a phishing scam and keep your email communications secure.
Attacks involving the takeover of user accounts
If your email password has been compromised in a data breach, you may be vulnerable to an account takeover attack. In this type of attack, a hacker gains unauthorized access to your email account and can use the information contained within it to access other, more sensitive accounts.
For instance, a hacker could use the information in your inbox to gain access to your online banking or social media accounts. They may also attempt to blackmail you using your emails or demand a ransom payment in exchange for restoring your account access, this is often seen in Sextortion scam emails.
Verifying if an email has been leaked
With data breaches becoming increasingly common, it’s essential to monitor your email for any signs of a leak. One useful tool for this is the Have I Been Pwned (HIBP) database, created by web security consultant Troy Hunt. This website allows you to check whether your personal information, including your email address, phone number, and password, has been compromised.
To use HIBP, simply enter your email address and check the results. If your email address appears in the database, it means that it has been involved in a data breach, and you should take immediate action to secure your accounts.
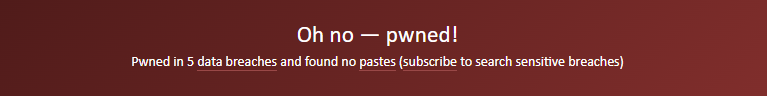
This message indicates that the email address has been included in a data breach
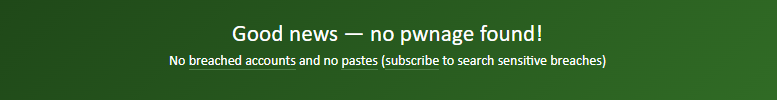
This message indicates that the email address has not been included in any data breaches.
In addition to using HIBP, it’s also important to be vigilant about phishing scams, avoid sharing personal information online, and use strong, unique passwords for each of your accounts.
Using an open-source password manager is the best way to remember multiple strong and unique passwords. Password managers generate and store complex passwords for each of your online accounts, making it difficult for hackers to crack them. With a password manager, you only need to remember a master password that allows you to sign in to your password manager.
Notable data breaches from popular services
Data breaches can expose not only your password and email but also other sensitive information. Unfortunately, many large companies fail to follow best security practices, leaving their systems vulnerable to hackers. With lax security measures in place, hackers can easily gain access to valuable data, potentially causing significant harm to both individuals and organizations. It is crucial for companies to prioritize cybersecurity and implement strong security measures to protect against potential data breaches and minimize the risks associated with cyberattacks.
There have been several significant data breaches over the years that have exposed sensitive information and affected millions of people. Here are some of the worst data breaches to date:
- Yahoo: In 2013 and 2014, Yahoo suffered two massive data breaches that exposed the personal information of over 3 billion user accounts, including names, email addresses, birth dates, phone numbers, and security questions and answers.
- Bell Canada: In 2014 and 2017 Bell Canada suffered a data breach via the hacker collective known as NullCrew resulting in the exposure of millions of customer records.
- Equifax: In 2017, Equifax, one of the largest credit reporting agencies in the US, suffered a data breach that exposed the personal information of over 147 million people, including names, Social Security numbers, birth dates, and addresses.
- LinkedIn: In 2016, this site owned by Microsoft had 164 million email addresses and passwords exposed. The passwords in the breach were stored as SHA1 hashes without salt, the vast majority of which were quickly cracked in the days following the release of the data.
- Twitter: In 2023, hackers were able to steal account details from over 200 million Twitter users and posted the database on a hacking forum.
- Marriott: In 2018, Marriott International suffered a data breach that compromised the personal information of up to 500 million guests, including names, addresses, phone numbers, email addresses, passport numbers, and credit card information.
- Capital One: In 2019, Capital One suffered a data breach that exposed the personal information of over 100 million people in the US and Canada, including names, addresses, phone numbers, credit scores, and Social Security numbers.
- Facebook: In 2018, Facebook suffered a data breach that affected over 87 million users and exposed their personal information, including names, email addresses, birth dates, and locations, to Cambridge Analytica, a political consulting firm.
Why and how to enable two-factor authentication for your online accounts
When it comes to protecting your online accounts, relying solely on passwords is not enough. Two-factor authentication (2FA) provides an additional layer of security by requiring extra verification beyond just a password to access your accounts. This can be in the form of a security key, a mobile device, or biometric information like your fingerprint or faceprint.
If possible, use a security key for 2FA, as they are more secure than one-time codes generated by an authenticator app. Security keys like YubiKeys can’t be spoofed, are not time-bound, and don’t require access to a mobile device. You can easily add them to your keyring and carry them with you everywhere you go. However, not all services support security keys.
Enabling 2FA and using a security key can significantly reduce the risk of unauthorized access to your accounts. Take the time to set up 2FA wherever possible and use a security key for the most secure protection.
Notify your contacts
To prevent your contacts from falling prey to phishing attempts that impersonate you, it is advisable to inform them about the possibility of receiving unusual emails purportedly from you.
If you had activated 2FA on your email account before the data breach and are sure that the perpetrator didn’t have access to your security key or authenticator app, you may skip this precautionary measure.
Thoroughly Examine Your Bank Accounts and Credit Card Statements
Regularly reviewing your bank accounts and credit card statements is a crucial step in protecting your sensitive data and preventing unauthorized access to your financial information. Scammers often exploit email leaks to achieve financial gain, targeting individuals with tactics designed to steal funds or commit fraud.
Look out for abnormal transactions, such as unfamiliar charges, significant expenses, or alterations to your billing address. Be especially wary of minor “trial payments,” typically ranging from $1 to $2, as these may be used by scammers to test the validity of your account before initiating larger fraudulent transactions.
If you detect any suspicious activity, contact your bank or credit card provider immediately. Most financial institutions will deactivate compromised accounts or cards and issue new ones to secure your financial information. By staying vigilant and monitoring your financial statements, you can quickly identify and address potential threats, minimizing the impact of a data breach on your finances.
Use a Strong Password that is unique
Using a strong, unique password for each account is one of the most effective ways to protect yourself online. Strong passwords are harder for hackers to guess or crack, especially when they include a mix of letters, numbers, and symbols. By making each password unique, you prevent a security breach on one account from compromising your other accounts, keeping your personal information safer across the board. Protecting your online identity starts with strong, unique passwords—it’s a small step with big security benefits. Try our Password Generator to create a secure password today.
Make use of email aliases
If you’re concerned about safeguarding your online privacy, using email aliases can be an effective strategy – particularly in the wake of an email breach. By leveraging an email alias, you can keep your primary email address private and minimize the amount of personal data you divulge online. There are two primary ways to create email aliases:
- Add a plus (+) sign: By incorporating ” + something” to your username, such as bobsmith+finances@thexyz.com, you can generate an email sub-address. This approach is also referred to as email sub addressing.
- Create a new email alias with a distinct username: You can create entirely new email aliases for each of your online accounts.
It’s worth noting that not all email service providers support these features, but Thexyz does – and we offer +aliases free of charge.
However, it’s important to be mindful that an email subaddress can be easily extracted by a malicious actor to launch spam campaigns or other attacks. To mitigate this risk, avoid using your actual name in your email subaddress.
Start using auto-aliases or bulk create multiple aliases
The better way to create new email aliases is to set them up individually. But given how many online accounts we use daily, it’s impossible to manually create new email aliases for all of them. It would also be a logistical nightmare to organize and manage that many inboxes. Thexyz also supports auto-aliases which are available to everyone using email without a custom domain.
Avoid opening links and attachments that appear suspicious
Phishing emails are a common tactic employed by cybercriminals to extract personal information or infect your device with malware. To safeguard against such threats, it is advisable to exercise caution and only open emails and attachments from trusted sources. Additionally, be wary of emails that urge you to take immediate action, such as making an urgent payment.
If you’re uncertain about the authenticity of an email, try reaching out to the sender via an alternate method, like calling their official helpline, and ask them to verify if they sent the email. If you suspect that you’ve received a phishing email, report it immediately to your email provider for prompt action.
Keep a regular check on your email address(es) for possible leaks
 Regular monitoring enables you to quickly identify and respond to any unusual activities or security incidents that could jeopardize your privacy.
Regular monitoring enables you to quickly identify and respond to any unusual activities or security incidents that could jeopardize your privacy.
An effective tool to help you stay alert is the “Notify me” feature provided by HIBP. By signing up for this service, you will receive notifications if your personal details are compromised in a data breach. Here’s how you can use it:
- Visit the Have I Been Pwned website.
- Click on “Notify me” located in the top navigation menu.
- Enter your email address and select the option to be notified of pwnage.
- You can also keep track of the latest data breaches by following HIBP’s Twitter account. Additionally, if you use a premium password manager, it may regularly search the HIBP database and notify you if any of your login details are compromised.
Select a reliable email provider that offers secure services
Your email provider is critical in protecting your inbox from unauthorized access and cyber threats, such as malware, phishing, social engineering, and hacking. At Thexyz, safeguarding your online privacy and enabling you to control your data is our top priority. Thexyz offers the following robust security features:
- Unlimited email aliases can be created with all email services at Thexyz, and all emails sent to your aliases will land in your inbox as usual.
- Thexyz security systems can temporarily lock your account if they detect any suspicious activity such as an attempt to hack your inbox.
- Security logs can be requested that record the IP address for each event in the security logs.
- Smart spam detection systems automatically detect spam emails and direct them to your spam folder. You can also add or remove email addresses from your Block List for granular control.
- Two-factor authentication (2FA) and security keys can be used to secure your account at Thexyz. We support authenticator apps that generate temporary codes, YubiKey, and other U2F/FIDO2-compliant keys.
- Anti-phishing protection is provided by N-Able, a set of advanced features designed specifically to combat phishing.
Anti-spoofing measures for custom domains include SPF, DKIM, and DMARC to protect you against spoofing attacks.






Thank you for sharing this informative article on protecting email privacy. I couldn’t agree more with the importance of remaining vigilant against impersonation attacks and phishing scams. It’s alarming how often people fall for these scams and end up compromising their personal information. It’s great to know that there are reliable and secure private email services available that offer advanced security features to prevent these types of attacks.
Great blog post, that pwned tool is very useful.
Staying vigilant and taking proactive steps to protect your email privacy is essential in today’s digital age. Thanks for sharing these helpful tips!
Great article on the importance of protecting email privacy! Phishing attacks are a serious concern for anyone who uses email, and it’s important to remain vigilant against these attacks. The tips provided here are very helpful, especially when it comes to being cautious of emails that request personal information or prompt you to click on links or download attachments.